Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

Private Keys are a string of alphanumeric characters and symbols that are used to create public keys and blockchain addresses and act as passwords to blockchain addresses.
Private Keys are a string of alphanumeric characters and symbols used to create public keys and blockchain addresses, acting as passwords to these addresses. When paired with a public key, they can be used to send, receive, and transact cryptocurrencies within the blockchain to which they belong.
Each blockchain address has its unique private key, which is intended to be visible only to the owner of that address. Loss of the private key results in the complete loss of crypto in the address or wallet.
Private keys serve two major purposes in blockchain.
First, they allow you to use your blockchain address or wallet securely. However, if you lose your private key, the cryptocurrency in that address is lost forever.
Second, private keys are used to generate public keys, which you use to receive cryptocurrency.
Private keys essentially allow you to spend the cryptocurrency associated with the blockchain address to which they belong. You just need to enter the private key either in its raw form or through recovery phrases. When you do so, you basically control all the crypto in that blockchain address or all addresses if the private key belongs to a wallet.
Private keys are also crucial to the functioning of blockchains, as they are used to generate public keys and addresses. Each private key, when processed through a hash function (unique to each blockchain), can give you a public address that can be used to receive crypto.
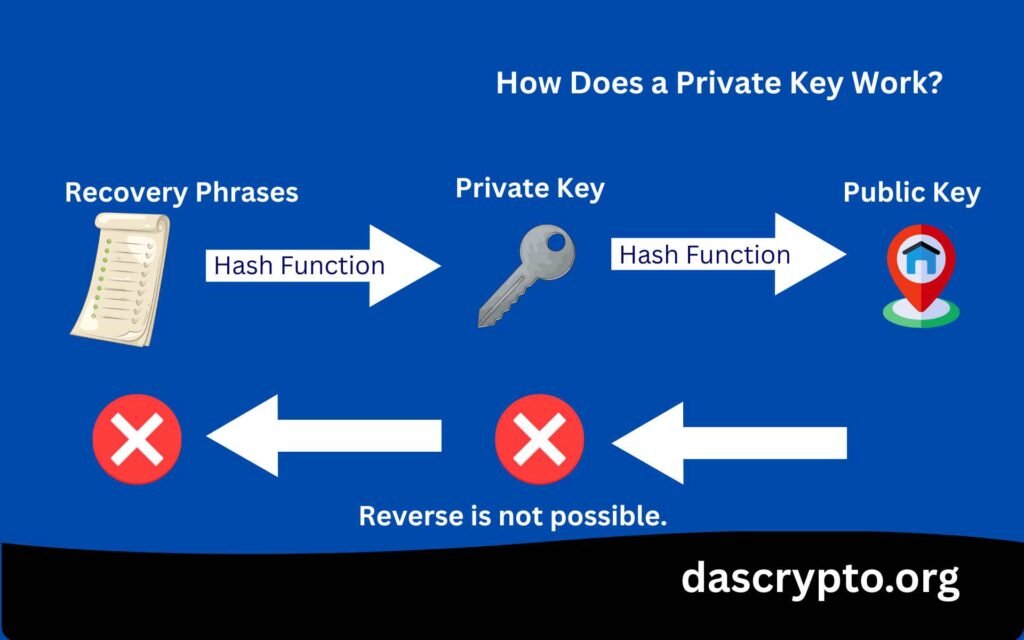
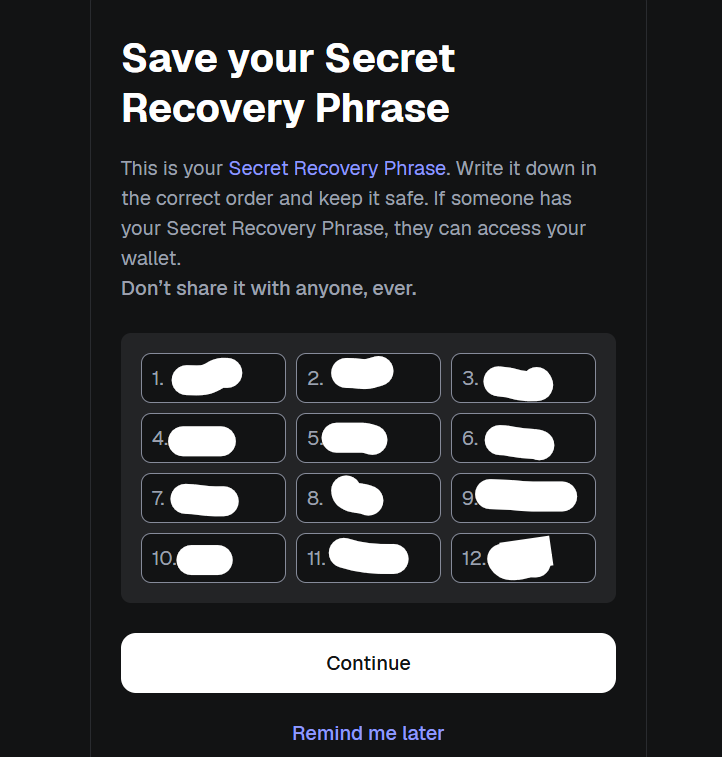
Private keys are created from random words in such a way that the hash function result of these words creates a unique string of alphanumeric characters and symbols. These words are called recovery phrases and are used to recover your wallet in case you forget its password or are changing devices, or for any other reason.
The hash function works in such a way that you can obtain private keys from secret recovery phrases, but not the other way. Similarly, you can obtain a public address from private keys, but not the other way. This means that you cannot obtain private keys from a public address or recovery phrases from private keys.
However, with the onset of quantum computing, this might change. Quantum computers might be able to break the current ECDSA encryption being used in cryptography.